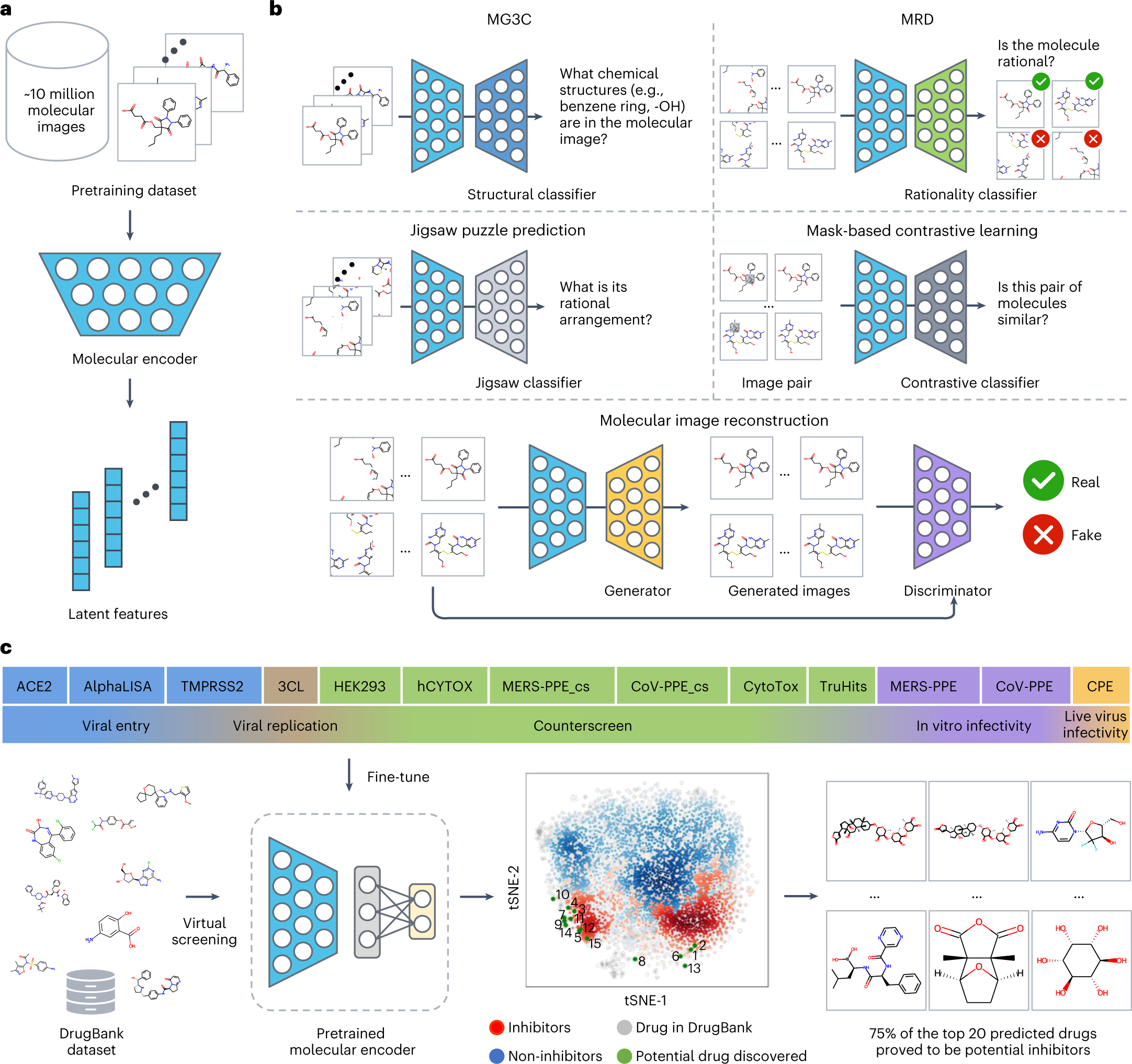
Accurate prediction of molecular properties and drug targets using a self-supervised image representation learning framework | Nature Machine Intelligence
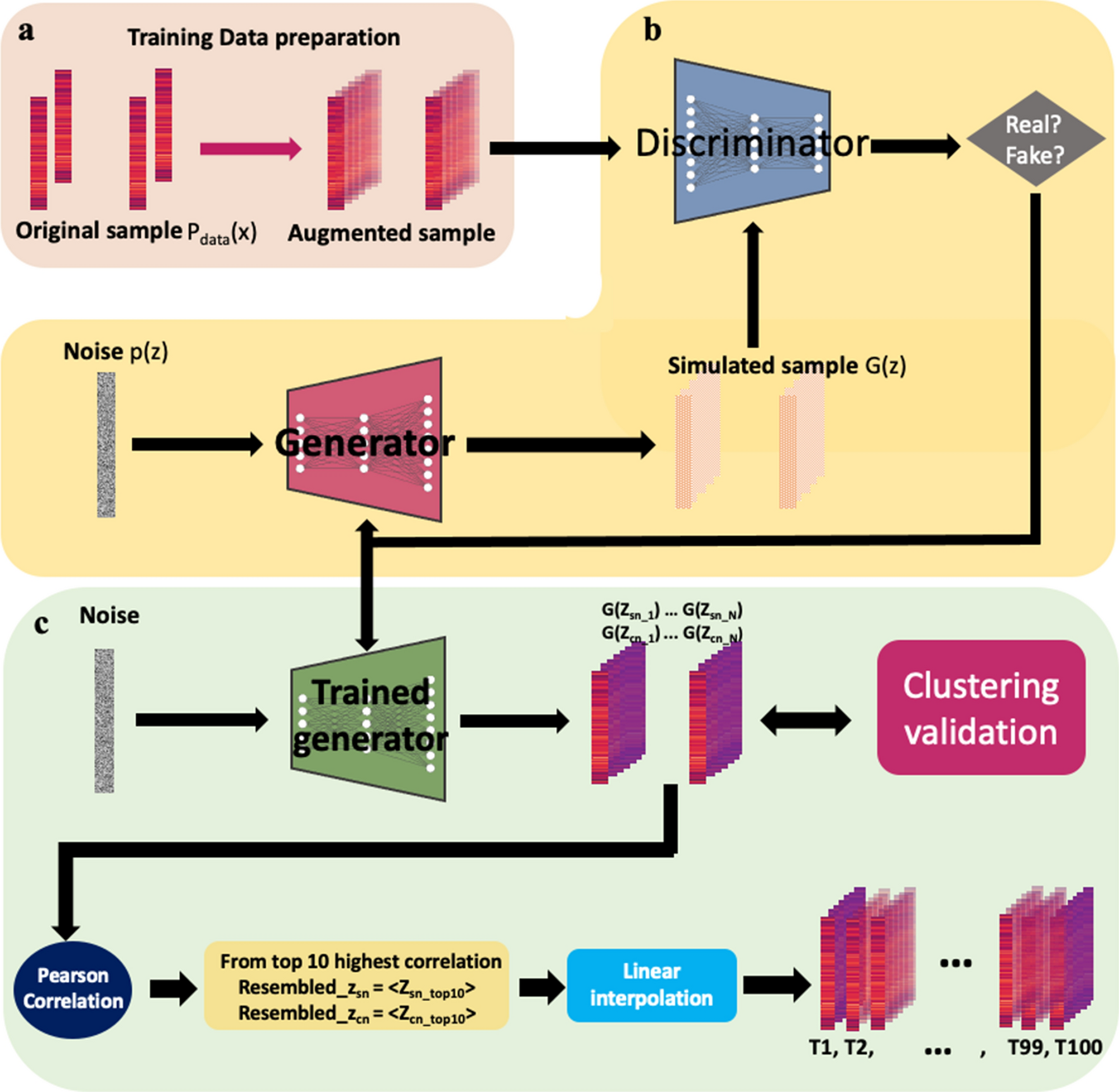
Unveiling OASIS family as a key player in hypoxia–ischemia cases induced by cocaine using generative adversarial networks | Scientific Reports
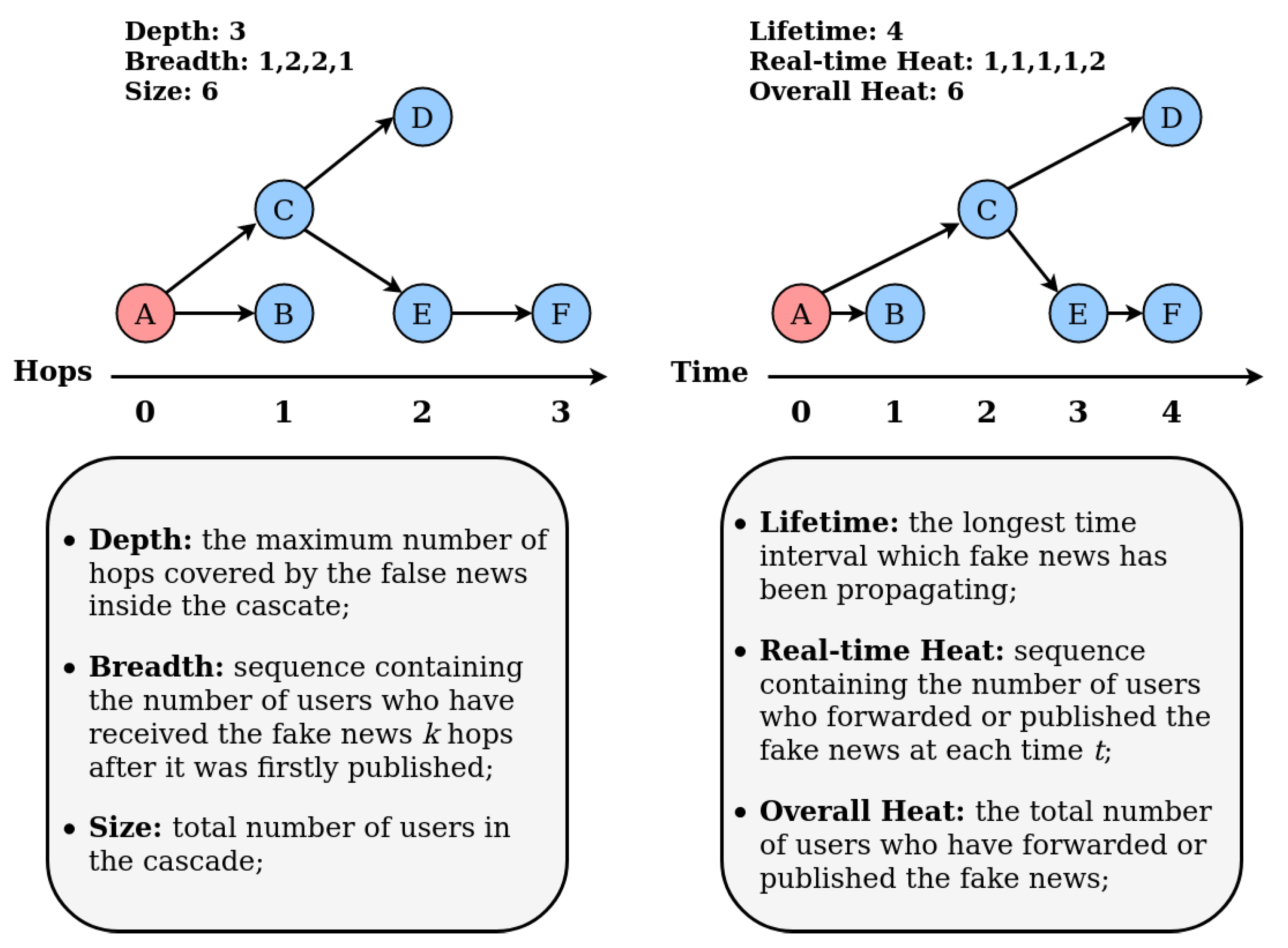
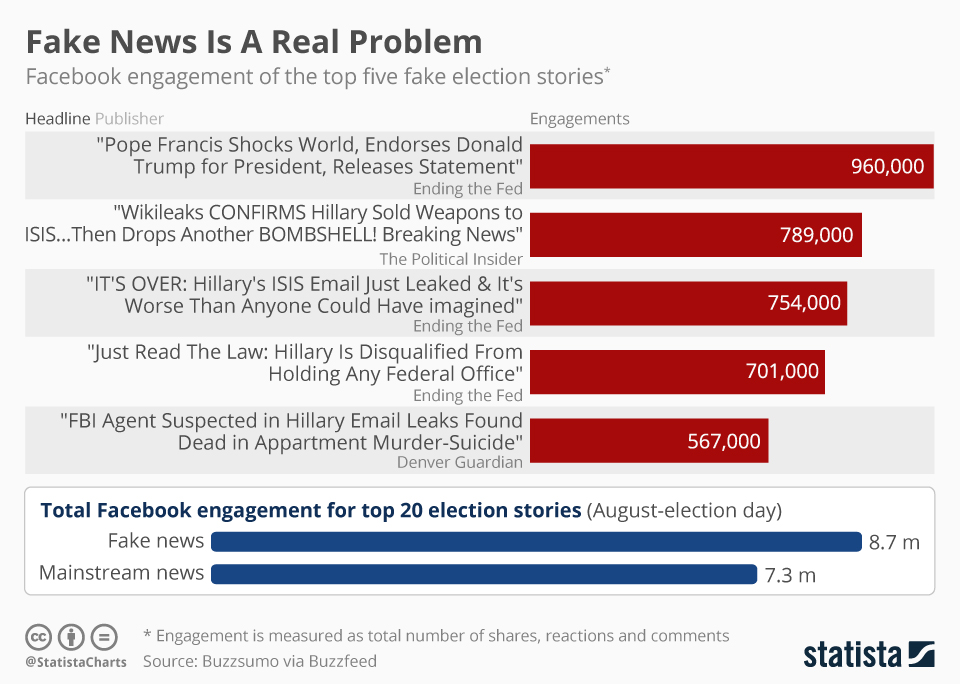
Information | Free Full-Text | Identifying Fake News on Social Networks Based on Natural Language Processing: Trends and Challenges

Drones | Free Full-Text | Adaptive Multi-Scale Fusion Blind Deblurred Generative Adversarial Network Method for Sharpening Image Data
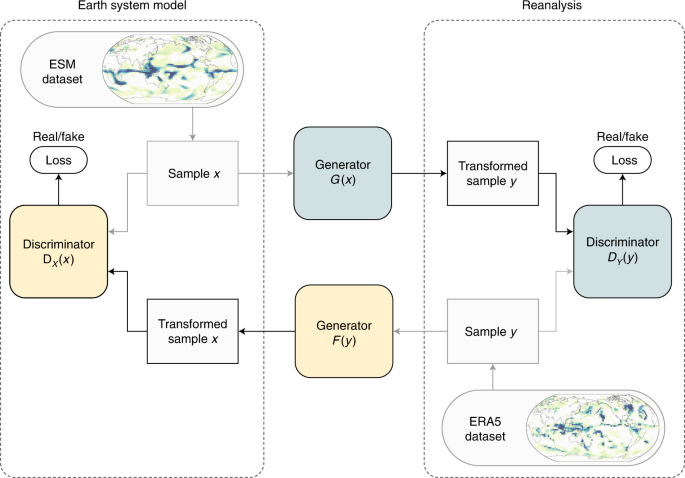
Physically constrained generative adversarial networks for improving precipitation fields from Earth system models | Nature Machine Intelligence

TasselGAN: An Application of the Generative Adversarial Model for Creating Field-Based Maize Tassel Data | Plant Phenomics

Attribution-Driven Explanation of the Deep Neural Network Model via Conditional Microstructure Image Synthesis | ACS Omega