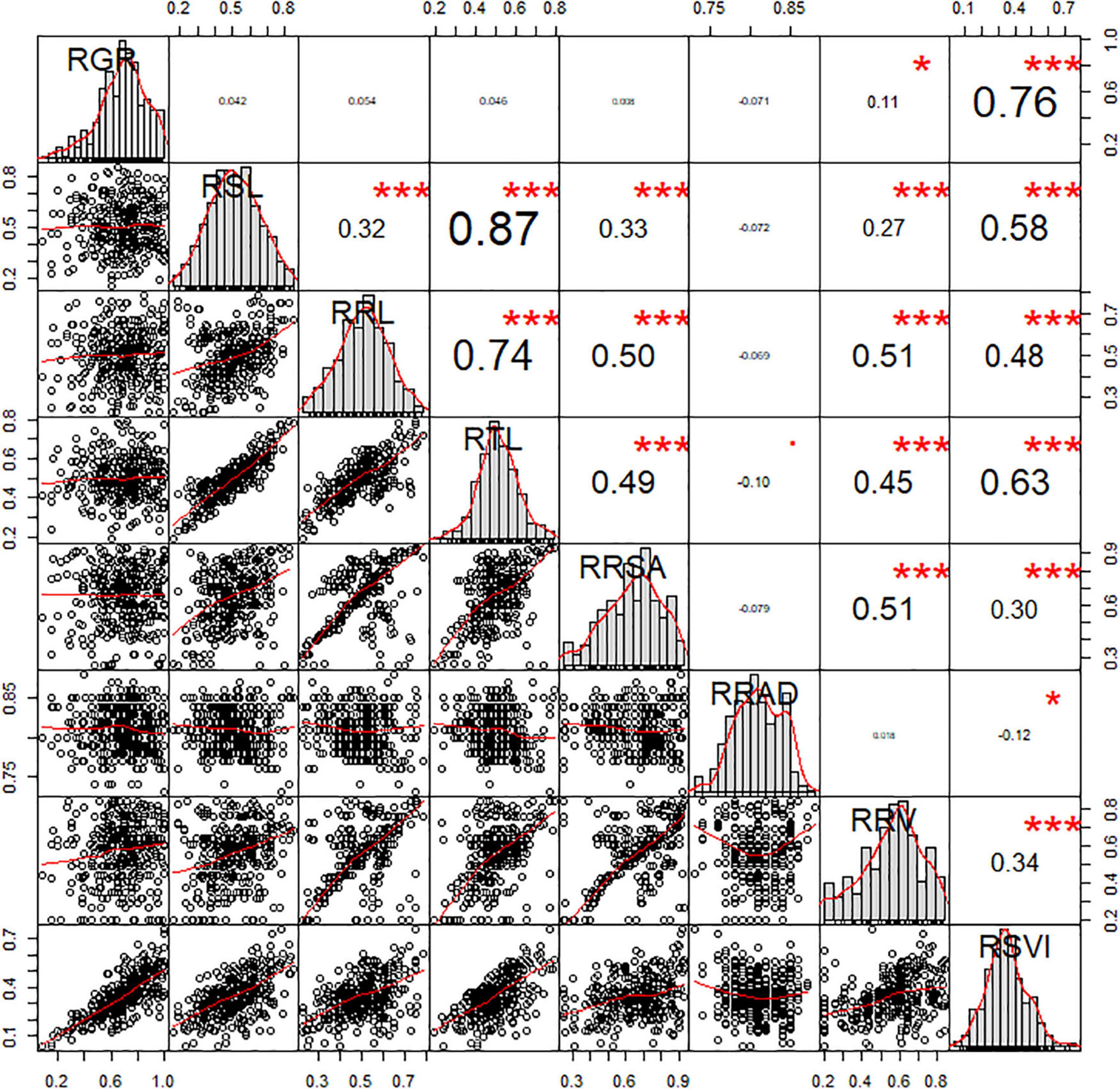
Frontiers | Using a high density bin map to analyze quantitative trait locis of germination ability of maize at low temperatures

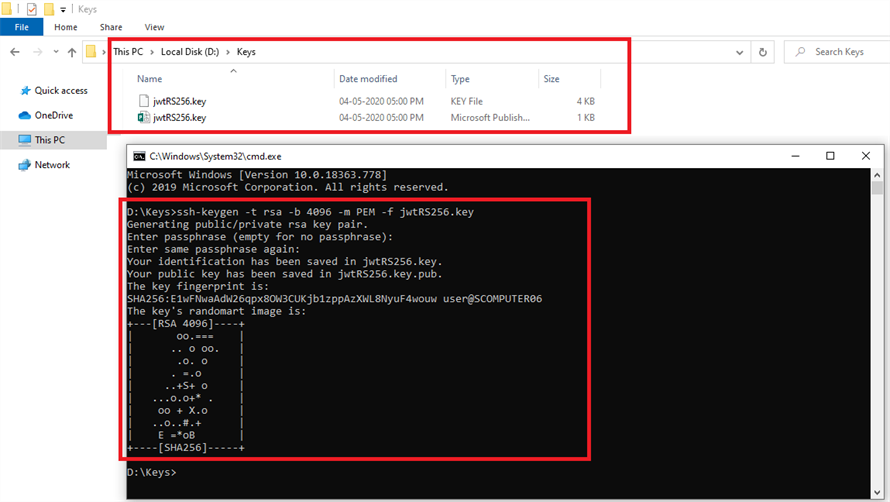
How to Remove Single Points of Failure by Using a High-Availability Partition Group in Your AWS CloudHSM Environment | AWS Security Blog

PDF) Prediction of Multi-Scale Socioeconomic Parameters from Long-Term Nighttime Lights Satellite Data Using Decision Tree Regression: A Case Study of Chongqing, China

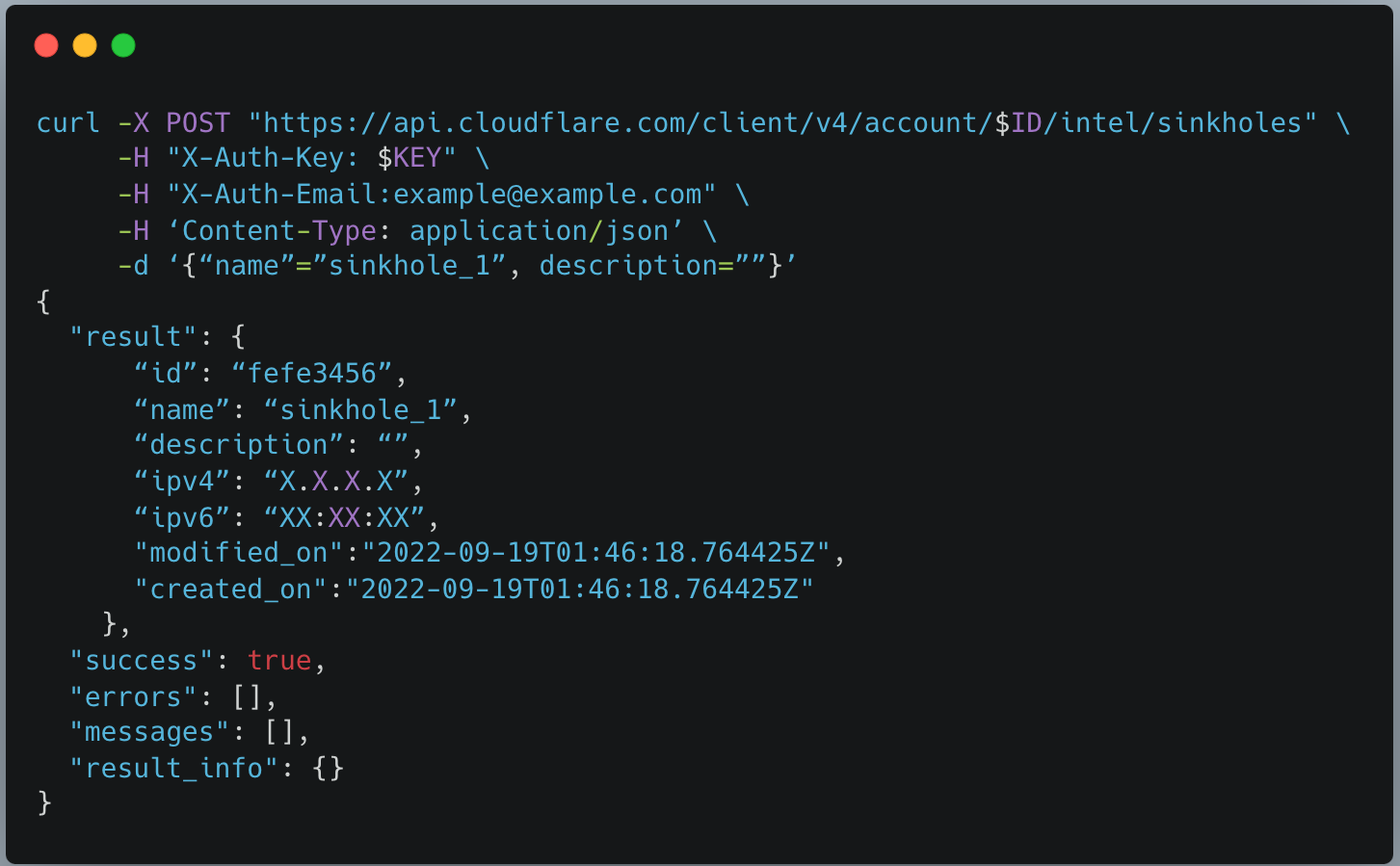
Symmetry | Free Full-Text | Homomorphic Comparison for Point Numbers with User-Controllable Precision and Its Applications



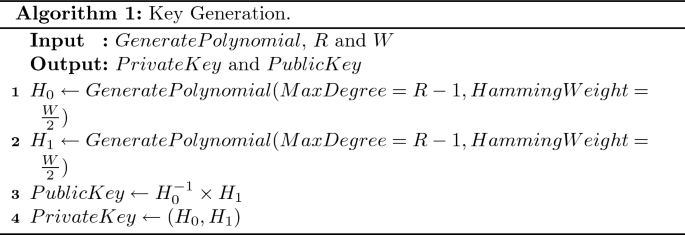
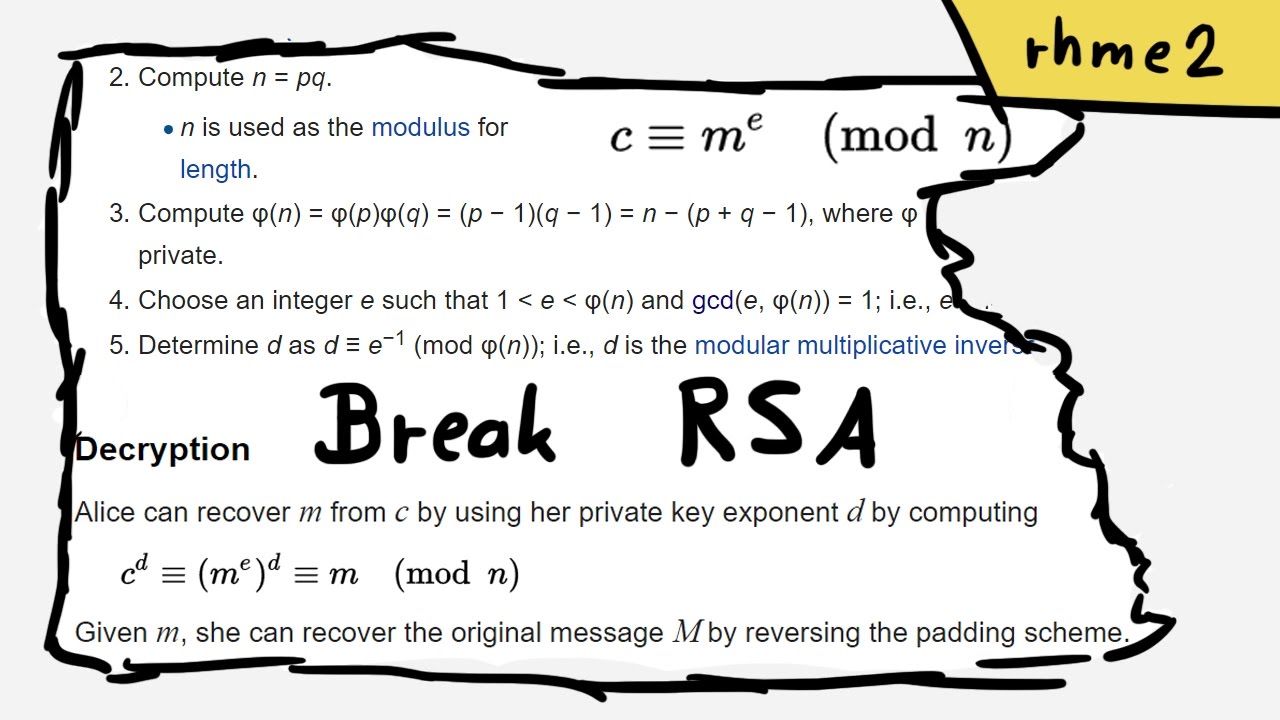
.png)